Security Breaches in Healthcare
This means any security breaches in healthcare that do not involve the acquisition or disclosure of unsecured PHI are not reported – even if they involve the acquisition or disclosure of data not classified as PHI because the data solely consists of individually identifiable non-health information or because the security breach occurred at an organization not subject to reporting requirements.
Additionally, because of the way in which the reporting requirements have been interpreted, some reported security breaches in healthcare may not have resulted in the acquisition or disclosure of unsecured PHI. This most often happens due to ransomware attacks in which there is no way of knowing whether data has been acquired or disclosed – so it is reported as a security breach anyway.
However, there are official statistics related to security breaches that are reported and recorded and these statistics reveal many trends.
How We Compiled Our Security Breaches in Healthcare Report
In 2009, Congress passed the Health Information Technology for Economic and Clinical Health (HITECH) Act. Section §16402 of the HITECH Act made it a legal requirement for entities covered by the Health Insurance Portability and Accountability Act (HIPAA) to report breaches of unsecured Protected Health Information to the Department of Health and Human Services.
The same section of the Act instructed the Secretary of Health and Human Services to publish a list of data breaches in which the unsecured Protected Health Information of more than 500 individuals is acquired or disclosed. This list can be accessed via the OCR Portal, and it is from this list we have complied most of our security breaches in healthcare report. Other sources are indicated below.
Caveats to our report include that reported security breaches in healthcare can be attributable to a series of factors. However, because of the way in which breaches are reported, many include only one of the factors or only one location from where data was acquired or disclosed. This not only applies to information provided by the OCR Portal, but by other sources as well.
Overall OCR Facts
- Since mandatory reporting started in 2009, there have been 5,187 HIPAA data breaches affecting more than 500 individuals reported to OCR.
- According to OCR data, the reported 5,187 HIPAA data breaches have resulted in the acquisition or disclosure of over 385 million records.
Breach types/number of breaches per year
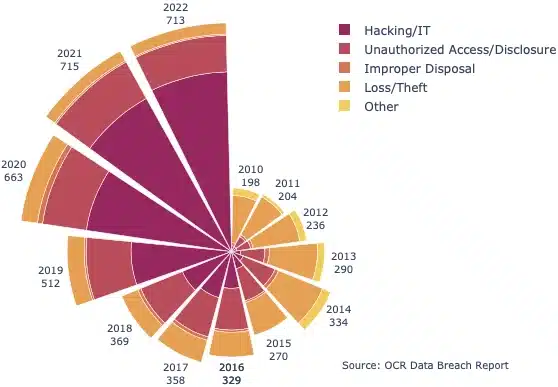
- The number of security breaches in healthcare has been steadily increasing – over 3.5 times as many breaches were reported in 2022 than in 2010.
- Since records began, just under half of incidents (47%, 2,490 incidents) were attributed to Hacking/IT incidents. A further 1,306 incidents (25%) were due to Unauthorized Access/Disclosure events, 1,267 were attributed to Loss/Theft (24%), 116 incidents (2%) were due to Improper Disposal, with other or unknown causes responsible for the remaining 111 incidents (2%).
- Until 2015, loss/theft breaches were the most reported to OCR; but in 2022 the number of reported loss/theft breaches is just a quarter of the 2010 figure (35 versus 147).
- Between 2010 and 2022, the number of Hacking/IT incidents reported to OCR grew by a factor of 70 from 8 to 560 – (Unauthorized Access/Disclosure: 11.4, Improper Disposal: 0.4, Loss/Theft: 0.25, Other: 1.2).
- In 2022, 80% of breaches reported involved a Hacking/IT incident, up from 4% in 2010
- Since 2014, more records have been breached due to Hacking/IT incidents than any other breach type.
- Loss/Theft used to be the leading cause of compromised records, but now affect relatively few individuals (less than 1% of individuals affected in 2022).
Number of individuals affected by breaches
- The number of records affected each year has increased steadily, largely due to the prevalence of Hacking/IT incidents: 18 times as many individuals were affected in 2022 relative to 2012 (52 million versus 2.8 million).
- More and more records have been affected by cybersecurity incidents in recent years: in 2022, 44 million individuals (84% of all those affected in 2022) had their healthcare data affected by a Hacking/IT incident. This is up from only 900,000 a decade before.
- Overall, since OCR records began, Hacking/IT incidents have affected 319 million individuals, Unauthorized Access/Disclosure has affected 25 million, Improper Disposal 2 million, Loss/Theft 36 million, and Other/Unknown 3 million.
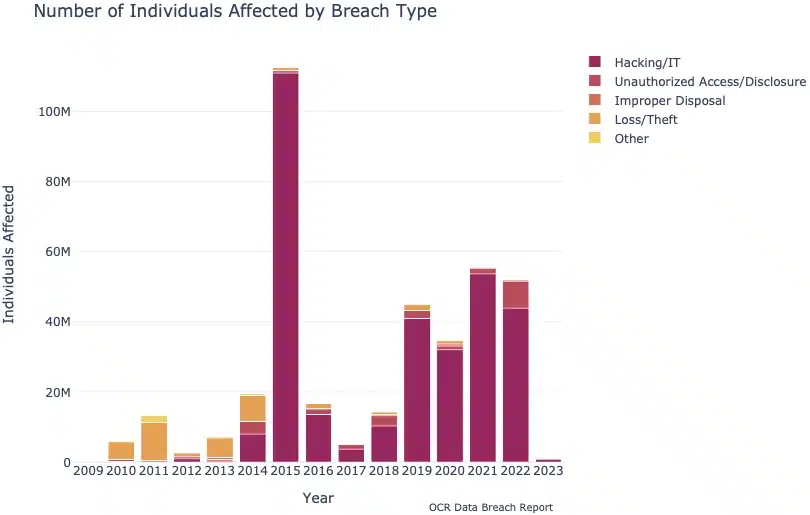
- Over 112 million individuals were affected by reported data breaches in 2015, the highest number for any year on record. Four of the ten largest ever reported data breaches occurred in 2015, which together accounted for 103 million records.
- The most significant data breaches on record are:
- Anthem Inc., 78.8 million records (2015)
- Optum 360, LLC, 11.5 million records (2019)
- Premera Blue Cross, 11 million records (2015)
- Laboratory Corporation of America Holdings, 10.3 million records (2019)
- Excellus Health Plan Inc., 9.3 million records (2015)
The cost of a data breach
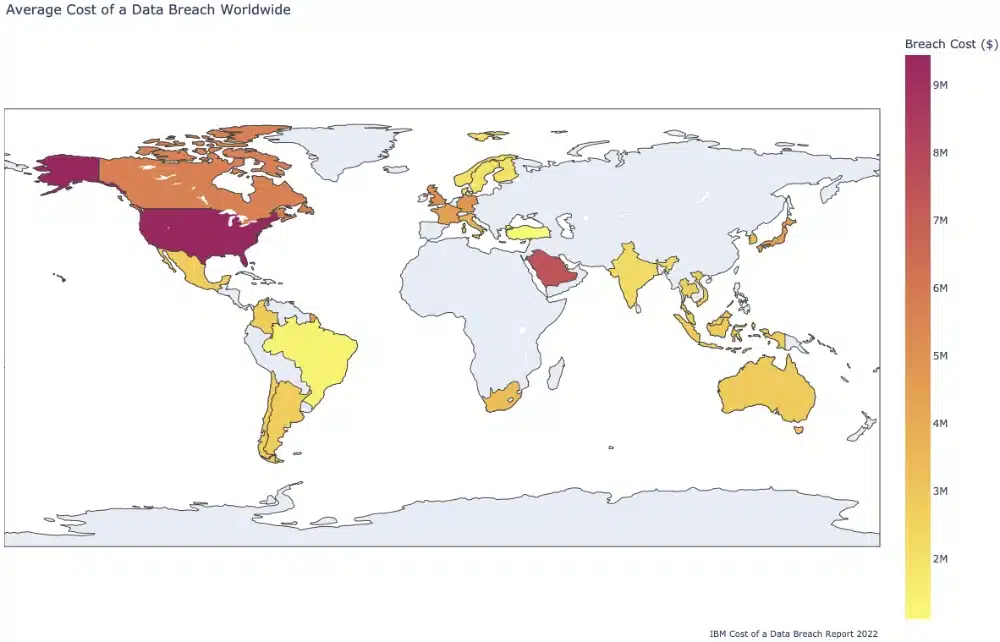
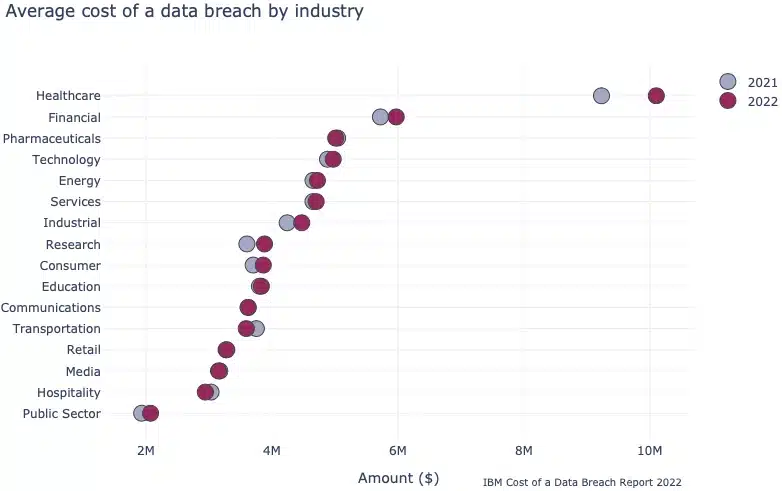
- The average cost of a data breach in the USA is $9.44 million – twice as much as the global average of $4.35 million (Source: IBM Cost of a Data Breach Report 2022)
- The global average cost of a healthcare data breach in 2022 was $10.10 million – up from $9.23 million in 2021. This is higher than any other industry, and nearly double the second highest (Financial, $5.97 in 2022; IBM Cost of a Data Breach Report 2022).
- About a third of the cost of the average data breach is due to lost business, a further third is due to expenses associated with detecting the cause of the breach, 27% is due to the post-breach response and about 7% is due to notifying affected and interested parties (IBM Cost of a Data Breach Report 2022).
- Globally, about 60% of businesses claimed data breaches have led them to increase the price of their goods or services (IBM Cost of a Data Breach Report 2022).
- Remote working can increase the average cost of a data breach by $1 million (IBM Cost of a Data Breach Report 2022)
Additional facts about data breaches
- Globally, insider breaches are nearly twice as common in the healthcare sector than in other industries (39% versus 20%, Verizon Data Breach Investigations Report)
- Across North America, insiders only accounted for 10% of breaches
- With regards to employee error – it is 2.5 times more likely for an employee to make a mistake which leads to compromised data than for them to intentionally misuse authorized access
- Financial gain was the primary reason behind global healthcare breaches (94%), with 4% being carried out for espionage purposes. About 1% of incidents were breaches of convenience, and a further 1% were motivated by grudges.
- HIPAA and GDPR are important factors for companies, with 29% of surveyed organizations citing the need to comply with these regulations as reasons for prioritizing cybersecurity frameworks. (ClearData State of Cloud Security in Health Providers).
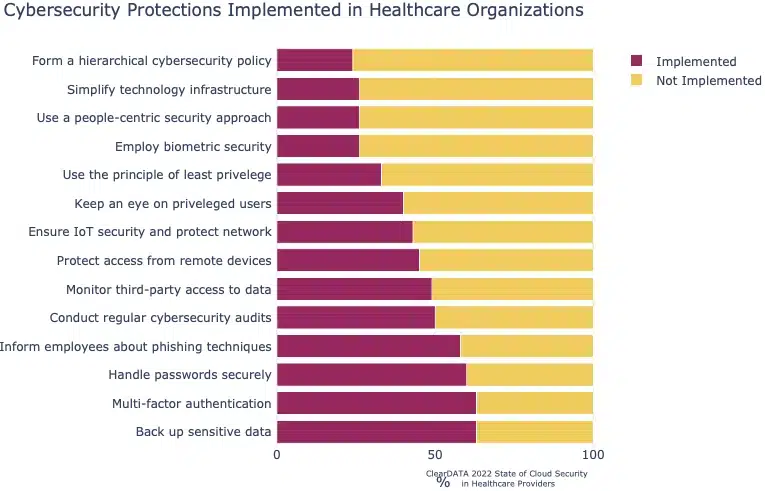
- Only 63% of healthcare organizations state they back up sensitive data. 63% use MFA, 60% have implemented password managers, 58% inform employees about phishing techniques, 50% conduct regular cybersecurity audits, 49% monitor third-party access to data, 45% protect access from remote devices, 43% ensure IoT security and protect network, 40% keep an eye on privileged users, 33% use the principle of least privilege, 26% employ biometric security, 26% use a people-centric security approach, 26% simplify technology and infrastructure, and 24% have deployed a hierarchical cybersecurity policy.
- In 2022, it took organizations an average of 207 days to identify a breach and 70 days to contain it (IBM Cost of a Data Breach Report 2022).
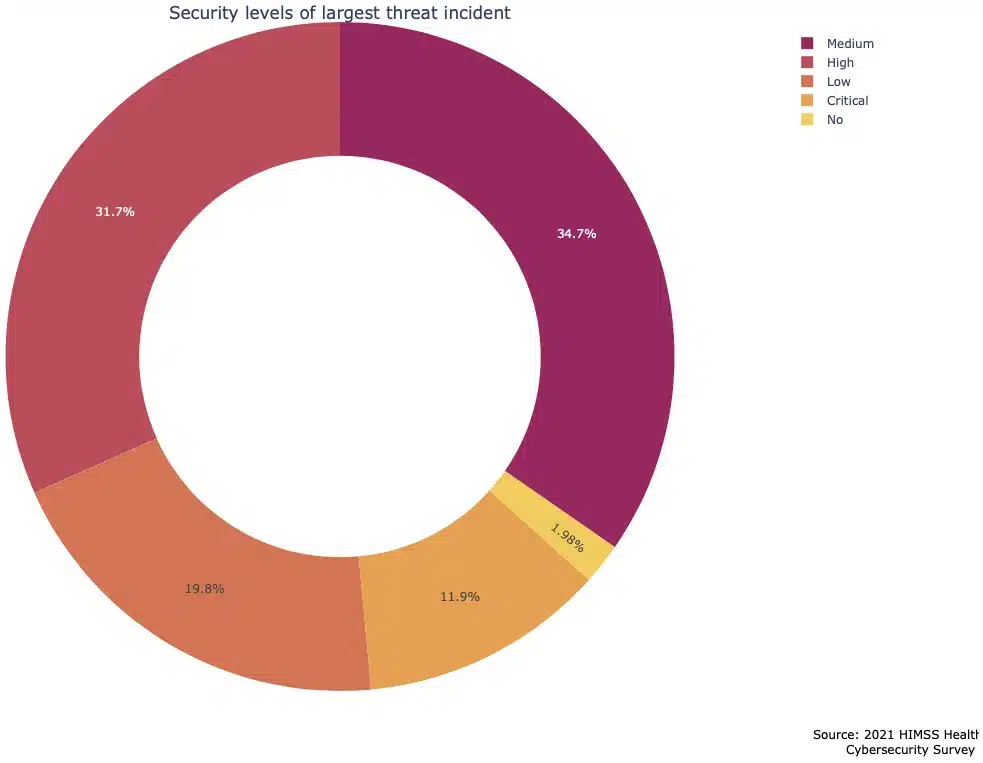
- Of the respondents to the HIMSS Healthcare Cybersecurity Survey, 67% of respondents said their healthcare organization experienced one or more significant security incidents in the last 12 months
- 44% of incidents were assessed as high/critical security levels, with a further 35% medium security, 20% low security and 2% ‘none’/no security level
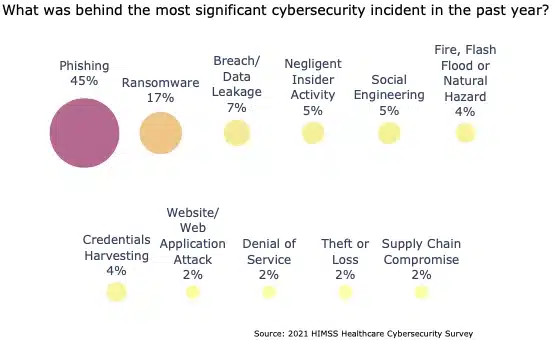
- The aforementioned “most significant data breaches” were attributed to: (HIMSS Healthcare Cybersecurity Survey 2021)
- Phishing attack: 45%
- Ransomware attack: 17%
- Breach or data leakage: 7%
- Negligent insider activity: 5%
- Social engineering attack: 5%
- Fire, flood, or natural hazard: 4%
- Credentials harvesting: 4%
- Website or web application attack: 2%
- Denial of service attack: 2%
- Theft or loss: 2%
- Supply chain compromise or attack: 2%
- In 52% of the most significant security incidents, the objective was to obtain financial information, with employee information and patient information targeted 43% and 39% of the time respectively. Intellectual property and confidential business information were targeted 15% of the time each, and biometric information in 6% of cases (HIMSS Healthcare Cybersecurity Survey 2021),
- Healthcare organizations reported the impacts of their largest security incidents to be:
- No/negligible impact: 44%
- Disruption of systems/devices impacting business operations: 32%
- Disruption of systems/devices impacting IT operations: 26%
- Data breach or data leak: 22%
- Disruption of systems/devices impacting clinical care: 21%
- Monetary loss: 17%
- Damage/destruction of systems/devices impacting IT operations: 6%
- Damage/destruction of systems/devices impacting clinical care: 4%
- Damage/destruction of systems/devices impacting business operations: 3%
- Other: 3%
Of course, it is always possible that there are consequences of which they are unaware.
(Source: HIMSS Healthcare Cybersecurity Survey 2021)
- In 2021, 41% of healthcare organizations spent less than 6% of their IT budget on cybersecurity (HIMSS Healthcare Cybersecurity Survey 2021)
- This has only decreased slightly from 45% in 2018
- 10% of respondents don’t know how much money is spent on cybersecurity from their IT budget
- 24% of organizations don’t have a specific cybersecurity budget
- Only 11% of organizations spent more than 10% of their IT budget on cybersecurity in 2021
- Between 2020 and 2021, 14% of healthcare organizations said that they increased their cybersecurity budget by 25% or more. A further 45% said they increased it between 5 and 24%. Budgets did not substantially change in 34% of organizations, and even decreased in 6% of cases (HIMSS Healthcare Cybersecurity Survey 2021)
- Nearly half (47%) of healthcare managers believe that budget constraints are among their biggest security challenges (HIMSS Healthcare Cybersecurity Survey 2021)
- 43% of managers also cite the failure of staff to comply with security policies and procedures to be a threat
- Only one in three healthcare organizations have fully implemented multi-factor authentication across their business,
- Only 38% of organizations have fully encrypted their “data at rest”, with half encrypting their data in transit
- Similarly, over one in five healthcare organizations (22%) have not “fully” implemented antivirus/anti-malware security controls
- Hospitals accounted for 30% of all large data breaches in the USA in 2020, costing approximately $21 billion (CyberMDX Perspectives in Healthcare Security).
- In 2020, large hospitals reported having to cease their operations due to security reasons for an average of 6.2 hours, costing them $21,500 per hour. Midsize hospitals were worse affected, closing for 10 hours on average at a cost of $45,700 per hour (CyberMDX Perspectives in Healthcare Security).
- In 2020, only 74% of organizations offered HIPAA training to staff to ensure the integrity of patient information was protected on virtual healthcare platforms (Deloitte: Virtual Healthcare Accelerated).
Location of breached information
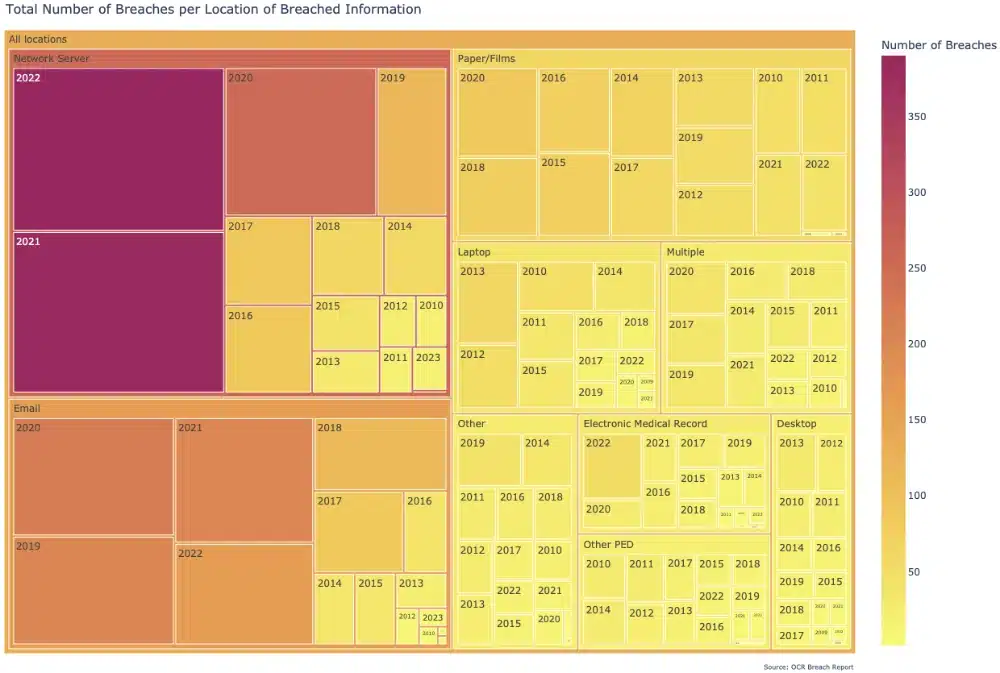
- Since 2009, the most common storage locations for information impacted by healthcare breaches healthcare organizations were:
- Network Server (1,587)
- Email (1,142)
- Paper/Films (790)
- Laptop (367)
- Multiple (336)
- Other/Unknown (303)
- Electronic Medical Records (237)
- Other Personal Electronic Device (229)
- Desktop (195)
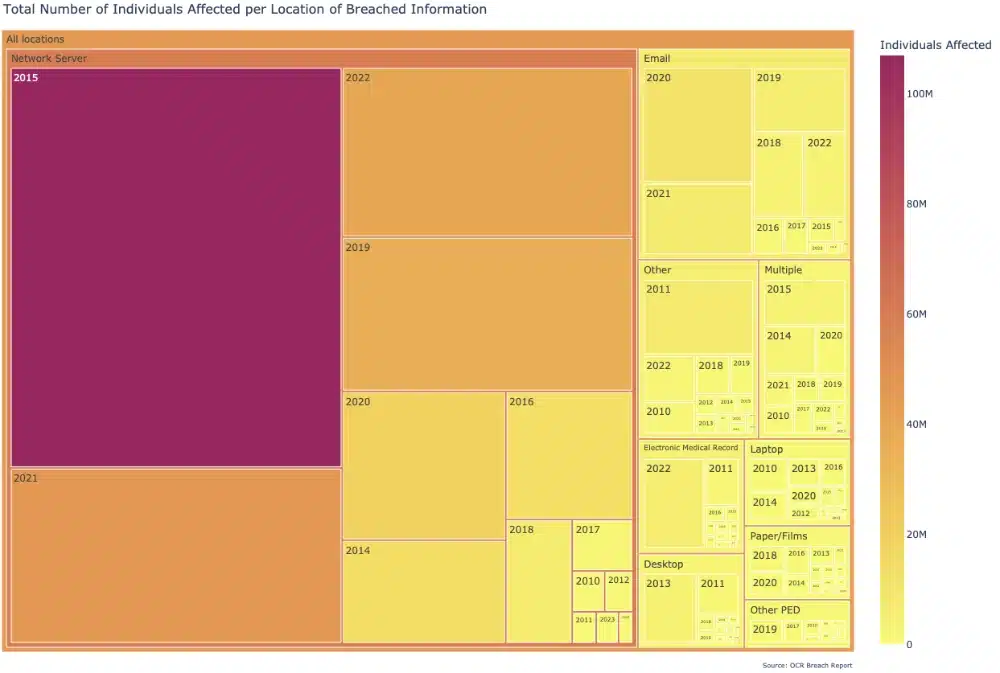
- The number of records impacted for each of these “breach locations” since 2009 were:
- Network Server: 288 M
- Email: 34 M
- Other: 16 M
- Multiple: 12.5 M
- Electronic Medical Records: 9 M
- Desktops: 8 M
- Laptop: 7 M
- Paper/Films: 6 M
- Other Personal Electronic Devices: 4 M
- Despite the fact that breaches where the data were stored on network servers only accounted for a third of the total breaches (1587 out of 5186), they accounted for a disproportionate number of affected records (288 million out of 385 million total, or 75% of the total). This was largely driven by breaches reported in 2015, which included four of the biggest data breaches on record (2015 had 107 million of the 288 million records for network servers in 2015).
- Less than 2% of all records affected were stored on paper/film despite it being the third most common location for breached information to be stored (790 breaches). It is harder to access huge amounts of patient data via these sources compared to Hacking/IT incidents.
- Since the HIPAA Privacy Rule came into force in April 2003, the Office for Civil Rights has received 322,579 HIPAA complaints (HHS.gov).
- Over 30,000 cases resolved by OCR required HIPAA covered entities and business associates to change their privacy practices or other corrective actions (HHS.gov).
- According to HHS.gov, most common issues HIPAA complaints made to OCR are:
- Impermissible uses and disclosures of protected health information
- Lack of safeguards of protected health information
- Lack of patient access to their protected health information
- Lack of administrative safeguards of electronic protected health information
- Use or disclosure of more than the minimum necessary protected health information
- Since March 2023, the OCR has referred 1,701 cases which potentially involve the knowing and wrongful disclosure or acquisition of individually identifiable health information in violation of the Social Security Act (§1177) to the Department of Justice for further investigation (HHS.gov).
- The five most common types of organizations that have been accused of violating HIPAA are, in order of frequency (HHS.gov):
- General Hospitals
- Private Practices and Physicians
- Pharmacies
- Outpatient Facilities
- Community Health Centers
Analysis of OCR and AG fines
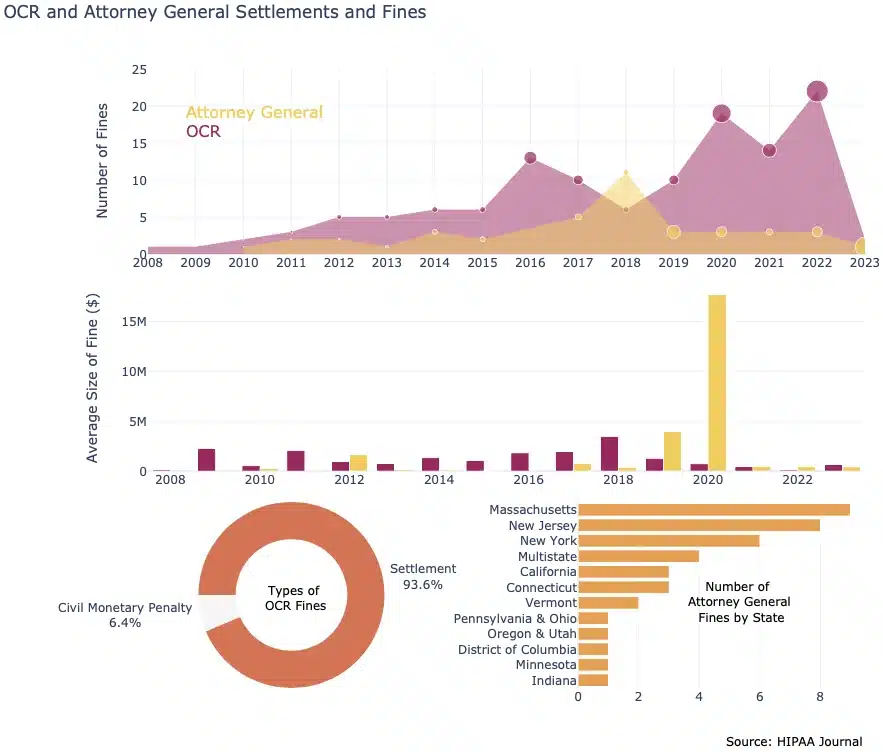
- Since 2008, OCR has imposed 125 fines or penalties, collecting a total of $131,019,890 (averaging $1,048,159) from covered entities found to be non-compliant with HIPAA Rules (HIPAA Journal).
- Of the125 fines imposed by the Office for Civil Rights (OCR), 117 (93.6%) were through settlements with the covered entity, and 8 (6.4%) were civil monetary penalties (HIPAA Journal).
- In 2018, Anthem Inc. paid $16,000,000 to settle OCR civil actions. This is currently the largest OCR settlement for a HIPAA-related security breach in healthcare (HIPAA Journal).
- State Attorney Generals have imposed fines totaling $79,376,986.59 against non-compliant HIPAA covered entities and business associates across 40 incidents (HIPAA Journal).
- The most significant fine ever imposed was the result of multi-state action against Anthem Inc. in 2020, as a result of the enormous 2015 data breach which involved nearly 80 million individuals (HIPAA Journal).
- The number of fines brought by state attorneys general against HIPAA covered entities is as follows:
- Massachusetts 9
- New Jersey 8
- New York 6
- Multistate 4
- California 3
- Connecticut 3
- Vermont 2
- Pennsylvania and Ohio 1
- Oregon and Utah 1
- District of Columbia 1
- Minnesota 1
- Indiana 1
Security Breaches in Healthcare: Conclusion
When reviewing our security breaches in healthcare it is important to put the data into context. For example, not all healthcare organizations have to report security breaches, security breaches that do not involve the disclosure or acquisition of PHI do not have to be reported, and the Department for Health and Human Services only maintain a publicly available list of breaches affecting 500 or more individuals. There could be many millions of smaller data breaches – or none at all!
Additionally, reporting entities can only attribute the cause of a security breach to the options available in the reporting portal. This means if a security breach is attributable to a brute force attack on a weak password, a misconfigured cloud storage bucket, or an open firewall port, the reporting entity is likely to assign the breach to the Hacking/IT category – even though they invited the security breach due to negligence. This limitation also affects how trends are identified from the raw data.
However, other considerations can also affect how trends develop. For example, the number of data breaches reported to the Department of Health and Human Services increased significantly from 2019 onward when the Jackson Health System was fined the maximum $1.5 million for violations of the Breach Notification Rule. This raises the question of whether there were more security breaches in healthcare from 2019 onward, or whether more security breaches in healthcare were reported.
Nonetheless, regardless of reporting limitations, inaccurate reporting, and misrepresentations, it is a fact that large security breaches in healthcare still occur. Healthcare organizations should make it a priority to reduce the number of security breaches and mitigate their consequences in order to best protect vulnerable individuals – and themselves – from loss, fraud, and medical identity theft.
